With an estimated 7.2 billion devices in 2020 in the enterprise sector and 13.5 billion in the consumer segment, standard PC security and anti-virus solutions will not be able to counter the challenges of cybersecurity threats on connected devices. Here is a list of companies that are currently providing security solutions and services for IoT and connected devices.
Verizon Enterprise Solutions
The company claims to provide Security Credentialing service that adds an extra layer of protection, over and above the customer/ client’s existing security. These IoT security services give security based on defense in depth, using digital certificates and other digital credentials. According to Verizon, IoT Security Credentialing helps in application protection to get an “over-the-top” (OTT) layer of security to help secure your IoT devices and apps, regardless of provider; it provides trusted authentication with select employees and even devices access to apps or IoT devices and data privacy to help keep an organization’s data secure through encryption.
Symantec
Claiming to already provide security to over a billion IoT devices, Symantec states that in the connected era, its not just about getting an external solution but the security should be built in during manufacturing. With Symantec Embedded Security, Critical System Protection protects embedded operating systems, including Linux, QNX, and Windows Embedded operating systems, protect automotive, Industrial Control Systems (ICS), manufacturing equipment, ATM, Point of Sale (POS), and medical devices helps secure and manage devices and communications, and deliver analytics to detect stealthy, sophisticated advanced threats to IoT systems.
BitDefender Box
Personal and enterprise antivirus and security solutions provider BitDefender recently released a product called the Bitdefender Box, an internet security solution product that incorporates hardware, cloud and software designed to protect smart home and connected devices. Created for personal use, the box claims to secure smart phones and smart TVs and all other home appliances and gadgets connected to the internet.
The device states that it does vulnerability assessment, URL Blacklisting and lets the user access and control the home network remotely through a smartphone.
Kramba Security
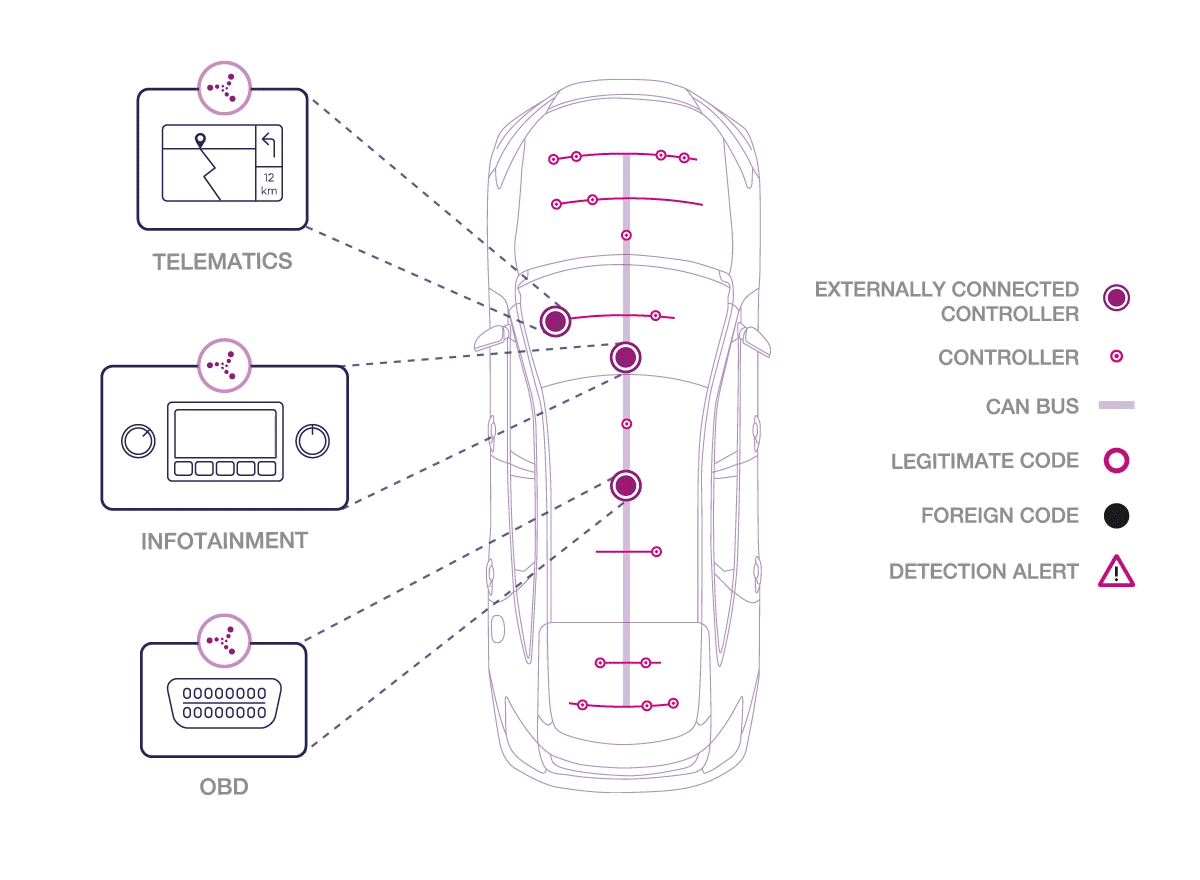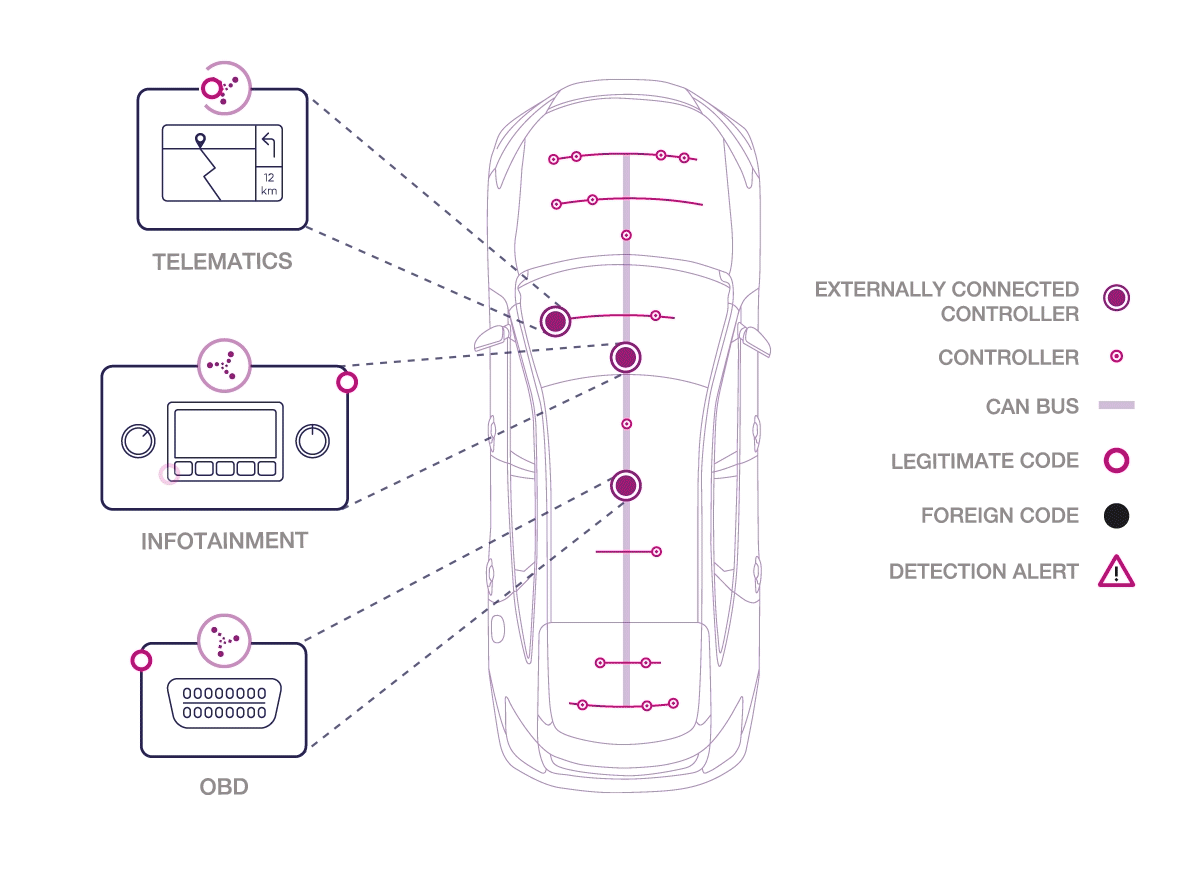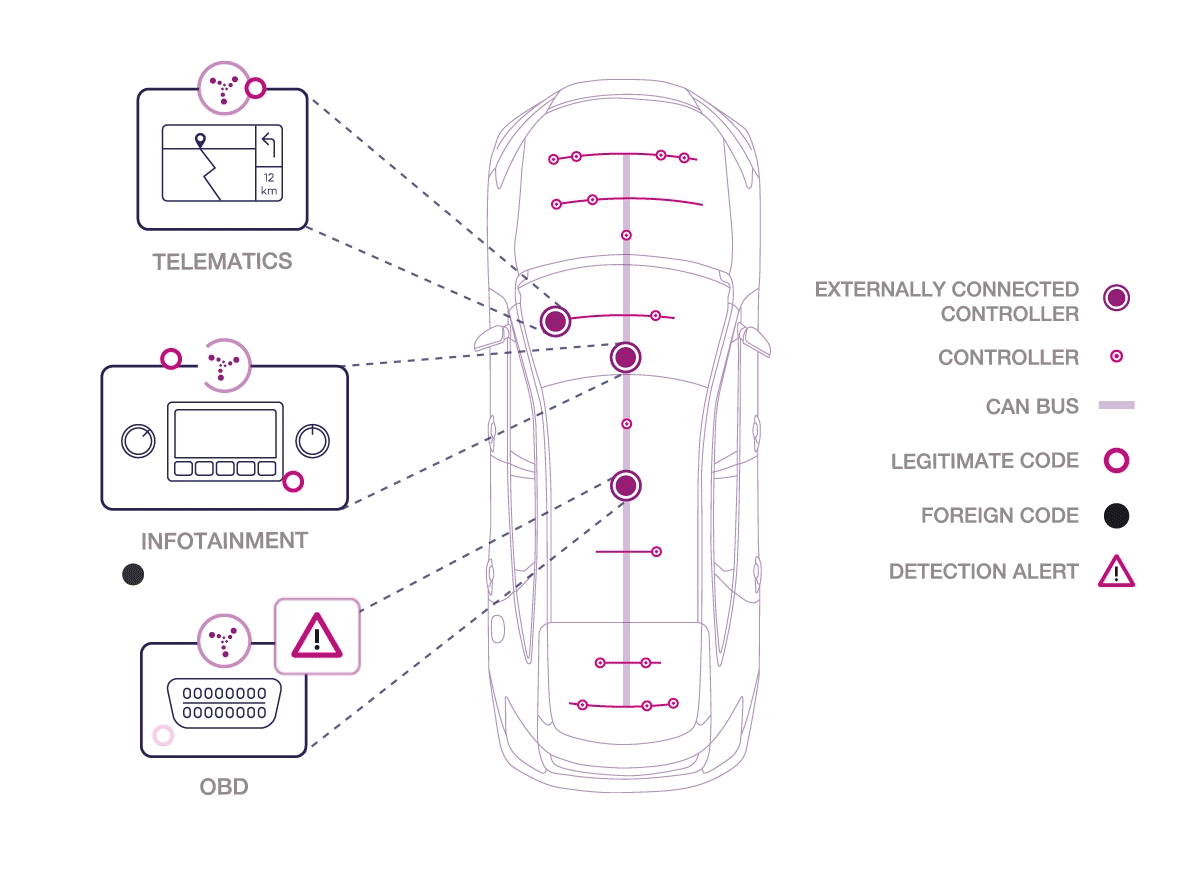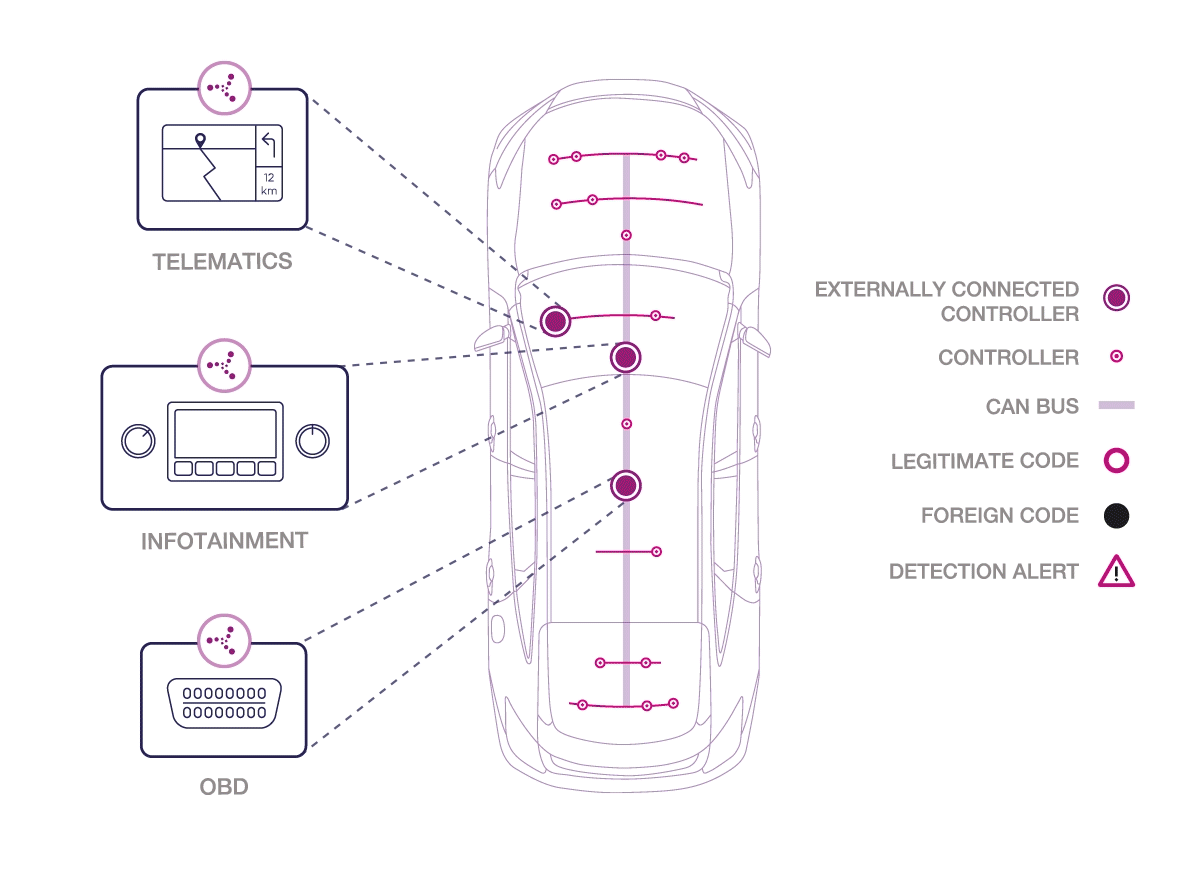
Karamba Security states that connected and autonomous cars can turn dangerous, as they may become targets for cyber attacks. Hackers can exploit external connectivity capabilities to take control of vehicles, endangering lives. Each car’s externally connected electronic control unit (ECU) represents a separate point of vulnerability to a cyber attack. If one ECU is compromised, it’s a gateway to every other ECU in the vehicle. To protect the lives of drivers, passengers and pedestrians, ECUs must be hardened against cyber attacks at all times. Karamba Security claims to offer Electronic Control Unit endpoint security to protect the connected car. The company hardens the connected Electronic Control Units within automobiles to protect them from cyber attacks and ensure the car’s safe, ongoing operations.
Infineon Technologies

Infineon has developed a broad range of easy-to-deploy semiconductor technologies to counter growing security threats in the IoT. According to the company the solutions enable system and device manufacturers as well as service providers to capitalize on growth opportunities by integrating the right level of security without compromising on the user experience. Complemented by software and supporting services, our hardware-based products create an anchor of trust for security implementations, supporting device integrity checks, authentication and secure key management. The company provides security solutions for smart homes, connected cars, industry automation and Information and communication technologies.
Gemalto
The company claims to be working with enterprises, industrial OEM, consumer OEM, mobile network operators and cloud service providers, to have a holistic view on the different building blocks like software, hardware and data for building a secure IoT ecosystem. Gemalto believes in three pillars for securing IoT devices, ensuring information is secure at rest and in motion. It states that its armory protects the device from design and manufacture, through its entire lifecycle, guarding data against malevolent attack. By providing security at the device end, security for the cloud and security lifecycle management (three pillars) the company, in the machine to machine field helps customers securely connect assets from edge to enterprise using Cinterion M2M modules, MIMs, and the SensorLogic platform. The company also provides security for automotive, health, wearables in the consumer IoT sphere.
DigiCert
The company believes that correctly implemented, PKI (Public Key Interface) can build and support security and trust in IoT ecosystems and connected devices. PKI’s role in IoT provides strong identity authentication and creates the foundation of trust that systems, devices, applications, and users need to safely interact and exchange sensitive data. DigiCert IoT solutions claim to deliver the critical authentication of users, systems, and devices without the need for tokens, password policies, or other user-initiated factors ensuring connections with trusted users and devices. Its SSL encryption delivers the essential certificates that can be used to encrypt data in motion and secure information being communicated between systems and devices, and its signing services maintain that software, firmware, drivers, data, or configuration settings have not been altered or tampered with.
Trustwave

Trustwave states that its Managed IoT Security allows developers and providers of IoT products and services to find weaknesses in embedded devices, interface applications, back-end services, APIs, cloud clusters and the connections in between. The solution lets users close the loop from thing to cloud, as it monitors and secures infrastructure and services that empower delivery of IoT services to reduce compromise risk and protect customer data and privacy. The solution is used for developing, testing and hardening physical embedded products and prototypes and related protocols, communications and back-end services. It also finds weaknesses in web apps, mobile apps, servers and associated APIs that interact with IoT products and cloud clusters that store and process IoT data.
