Under the detection name Android/Spy.Inazigram these 13 applications were phishing for Instagram credentials and stealing them to a remote server. ESET claims that these apps seem to have originated from Turkey, some apps used English localization to target Instagram users worldwide and have been installed by 1.5 million users. Post notification by the company the apps were removed from the Google Play Store.

How does it work?
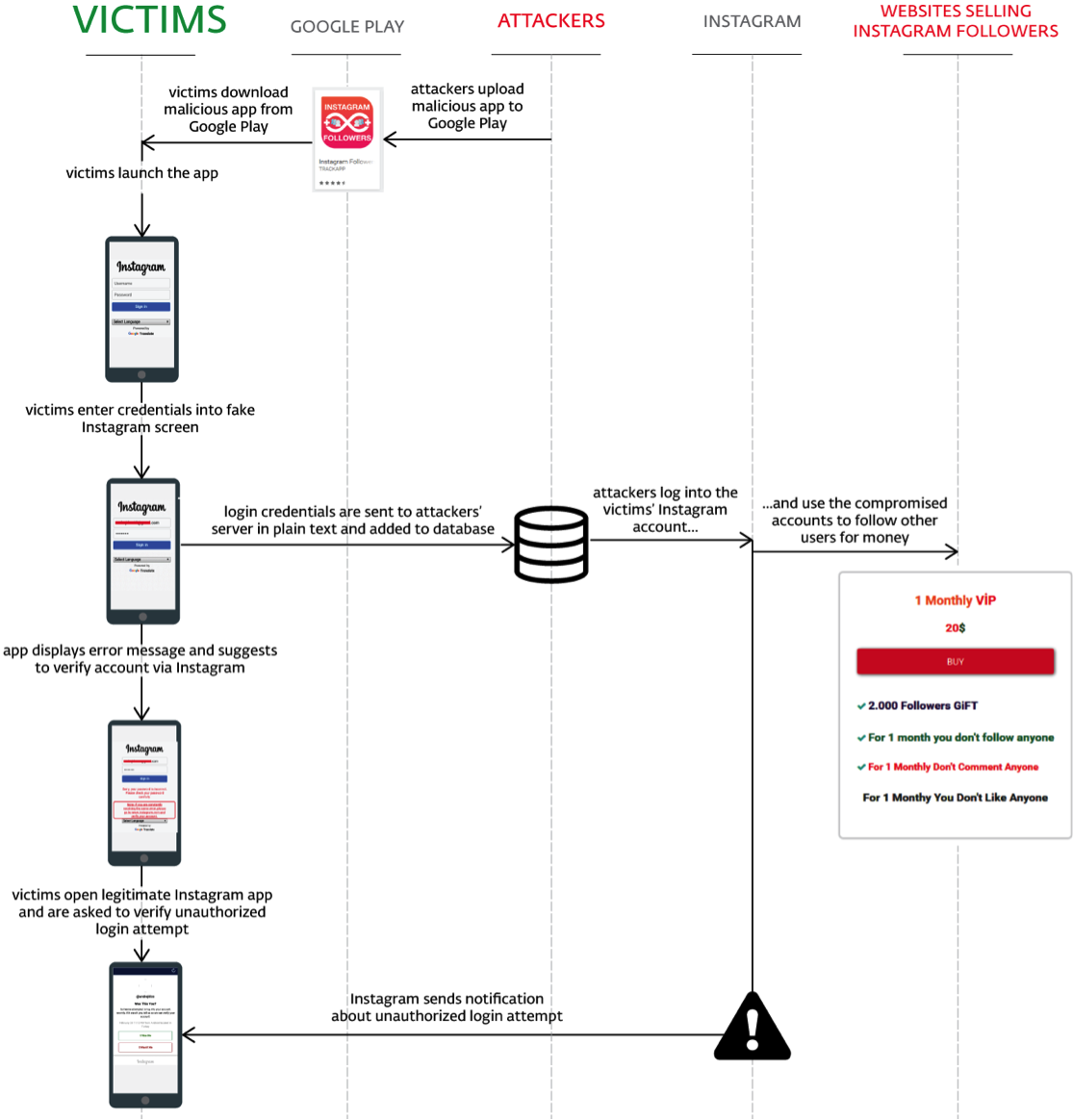
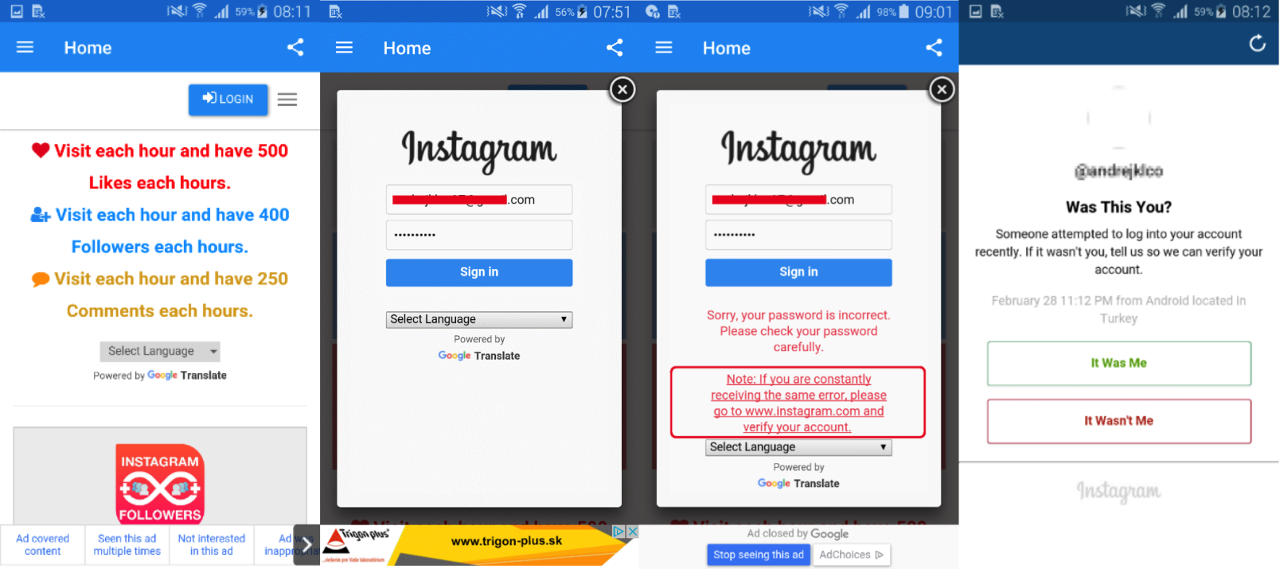
To lure users into downloading, the apps promised a rapid increase in the number of followers, likes and comments for an Instagram account.
The app required users to log in via an Instagram lookalike screen. The credentials entered into the form were then sent to the attackers’ server in plain text. After having entered the credentials, the user would find it impossible to log in, as the screen would show an error. The compromised accounts were used to raise follower counts of other users.
The error screen also featured a note suggesting the user visits Instagram’s official website and verifies their account in order to sign in to the third-party app. As the victims are notified about unauthorized attempt to log in on their behalf and prompted to verify their account as soon as they open Instagram, the note aims to lower their suspicion in advance.
What happens to stolen credentials?
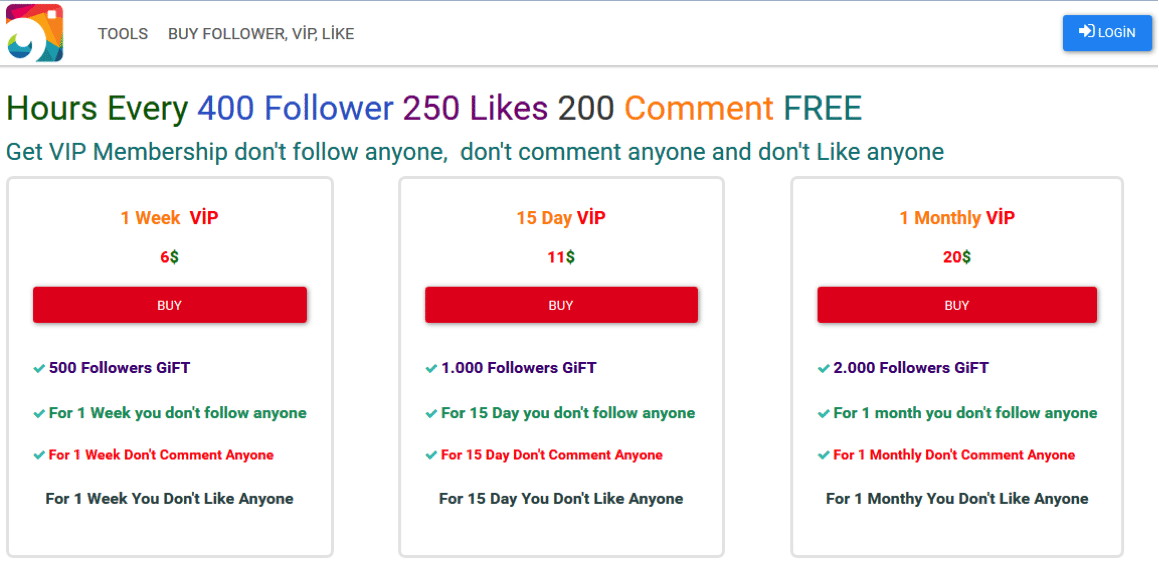
ESET believes that apart from an opportunity to use compromised accounts for spreading spam and ads, there are various business models in which the most valuable assets are followers, likes and comments.
The cybersecurity company states to have traced the servers to which the credentials are sent off and connected these to websites selling various bundles of Instagram popularity boosters.
All the applications employed the same technique of harvesting Instagram credentials and sending them to a remote server. Once a user went through the log in process, they would a notice from Instagram about someone attempting to log into their account. Interestingly, the Instagram account might appear to have increased following and follower numbers, but the user would be getting replies to comments which have never posted.
If the attackers were successful and the user did not recognize the threat upon seeing Instagram’s notification, the stolen credentials could be put to further use.
Increasing security measures
The company suggests that users should uninstall the apps from the application manager or use a reliable mobile security solution to remove the threats. Change the Instagram password and if the password is same for other platforms it should be changed as well, as malware authors are known to access other web services using the stolen credentials.
When downloading third party applications from Google Play Store, ESET states that users should not use sensitive information and check if the apps can be trusted by checking the popularity of the developer through the number of installs, content of its reviews and ratings.