According to Karamba, the US Assistant Attorney General for National Security had released a report that stated that connected cars will be the next battlefield. Gartner predicts that this segment will represent 250 million vehicles on the road by 2020. Karamba claims that connected cars have hundreds to thousands of hidden security bugs that hackers can exploit to infiltrate the vehicle, take control and compromise its safe operation.
“The risks to connected cars are real. Karamba Security’s automated sealing approach offers the automotive industry a tool to immediately detect and prevent cyberattacks that exploit software bugs in the code of connected cars. Thus, drivers can be confident they will always be in complete control over their vehicles, and manufacturers learn more about the frequency and nature of such attacks,” says Richard Wallace, Director, Transportation Systems Analysis, Center for Automotive Research.
How does Karamba Carwall software work?
Karamba’s patent-pending software seals the car’s ECUs by automatically creating security policies, based on factory settings. In real time, Carwall detects and prevents anything not explicitly allowed to load or run on the ECU, including in-memory attacks. Karamba claims of no ambiguity and no false alarms, detecting and preventing attackers, who try to exploit vulnerabilities and get into the car’s network.
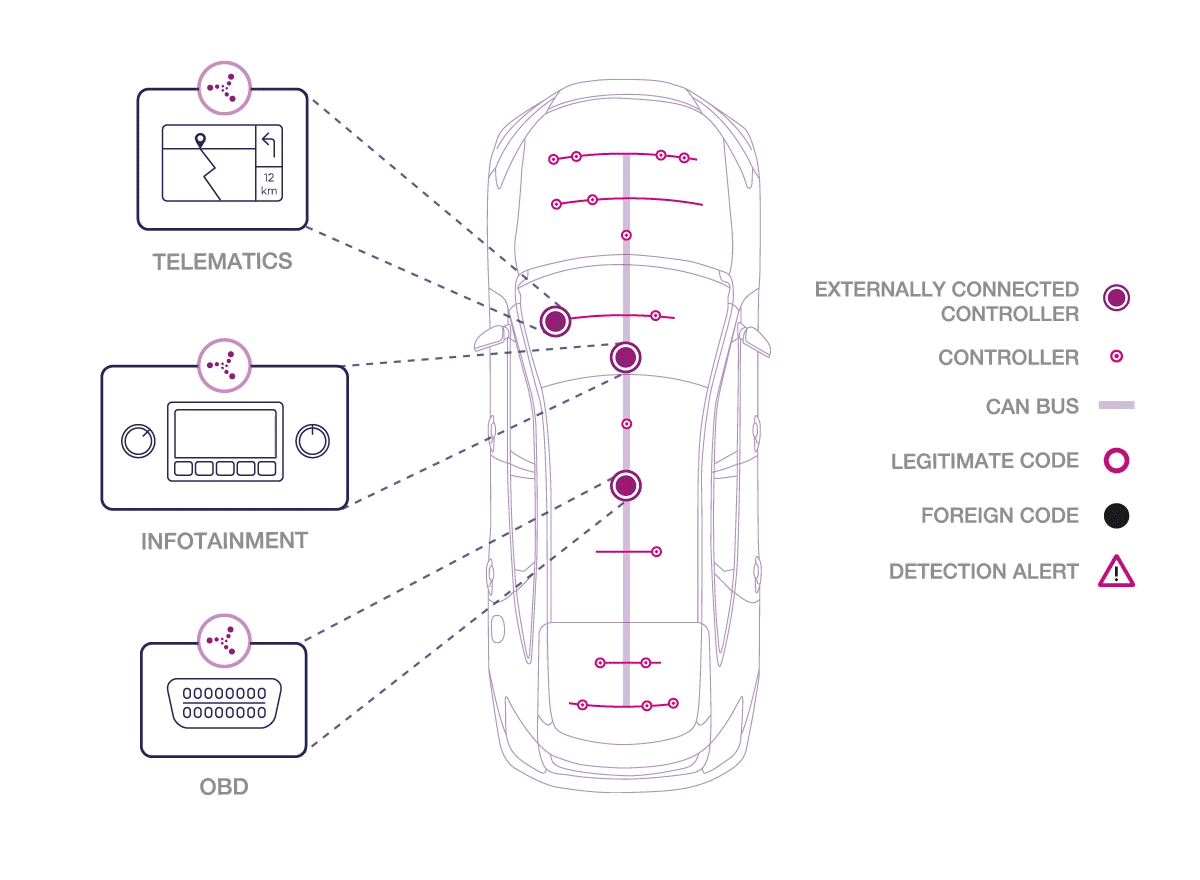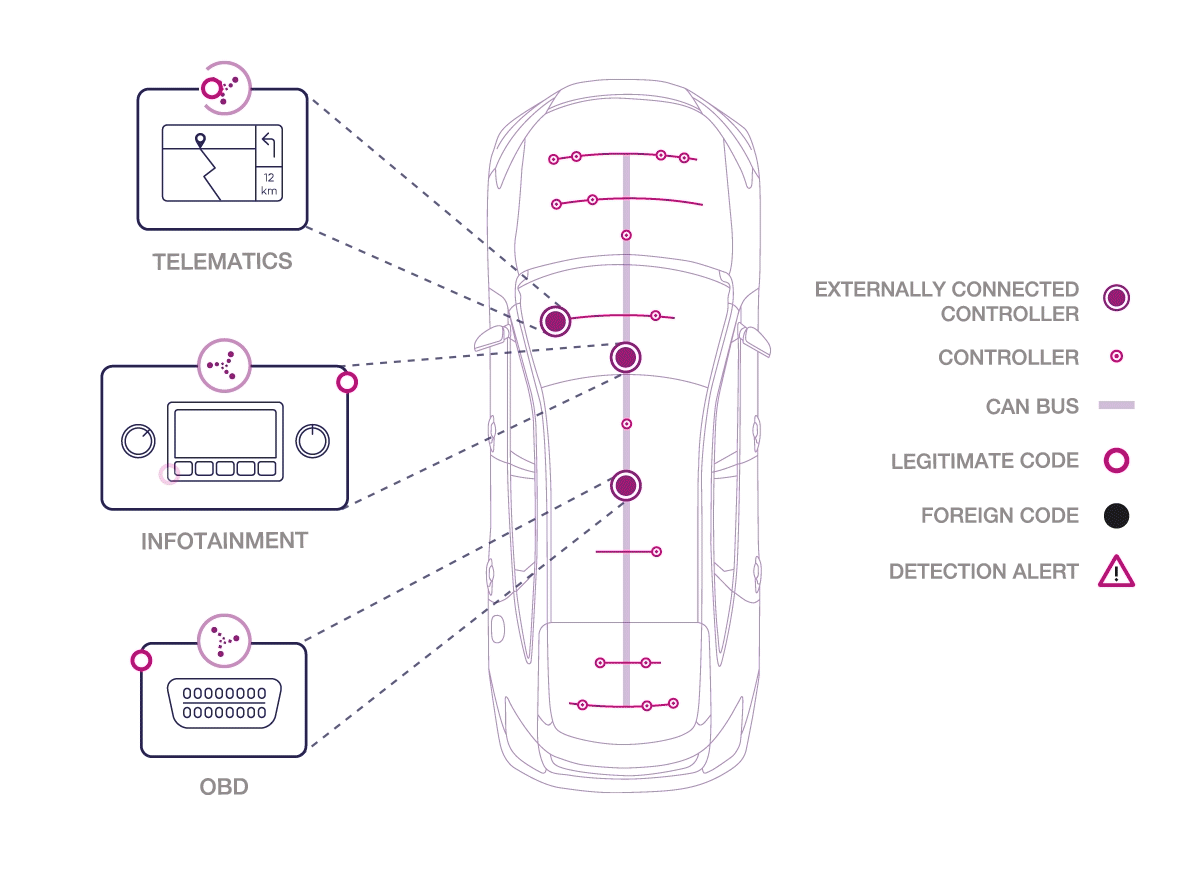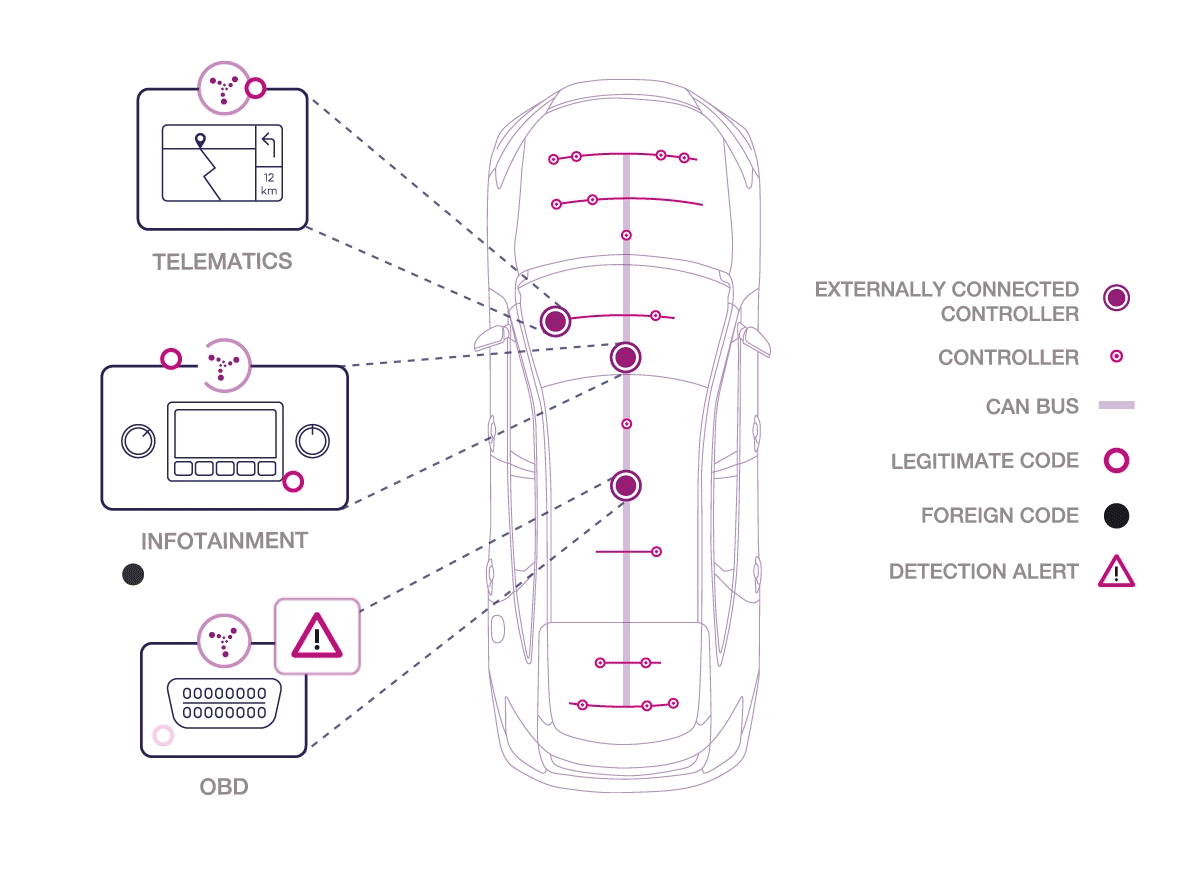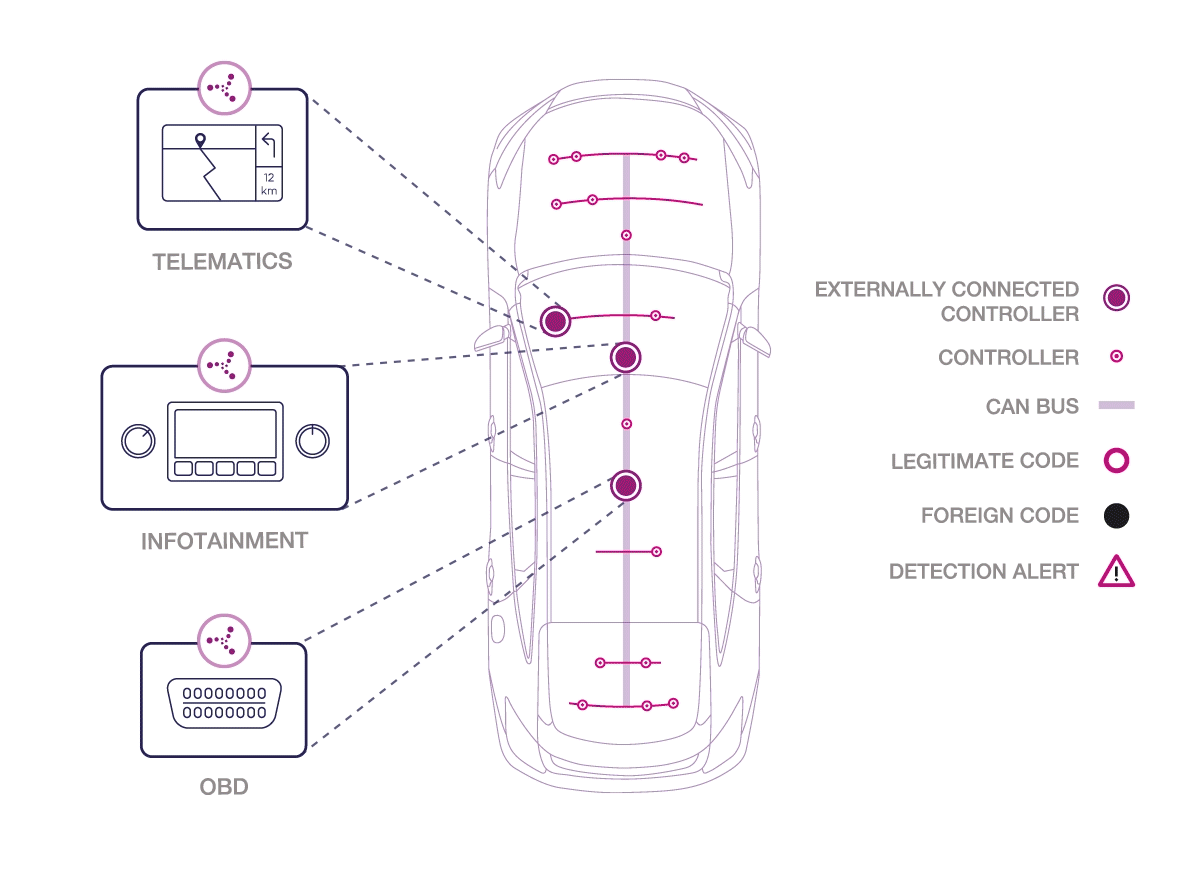
“Karamba’s Carwall enables car manufacturers to immediately address security bugs in existing or new code and eliminate an attacker’s way into a connected car. We give car manufacturers and Tier 1 system developers the tools to detect and seal their code against exploits and detect and stop attackers before they can ever get started,” says Ami Dotan, CEO, Karamba Security.
According to the company the Carwall software requires no developer resources as it is embedded during the ECU’s software build process, so it simply becomes part of the regular development cycle. As a result, Carwall makes it easy to secure and retrofit automobiles on the road and protect them from cyber-attacks. It can also easily be part of software updates completed during a regularly scheduled service visit.
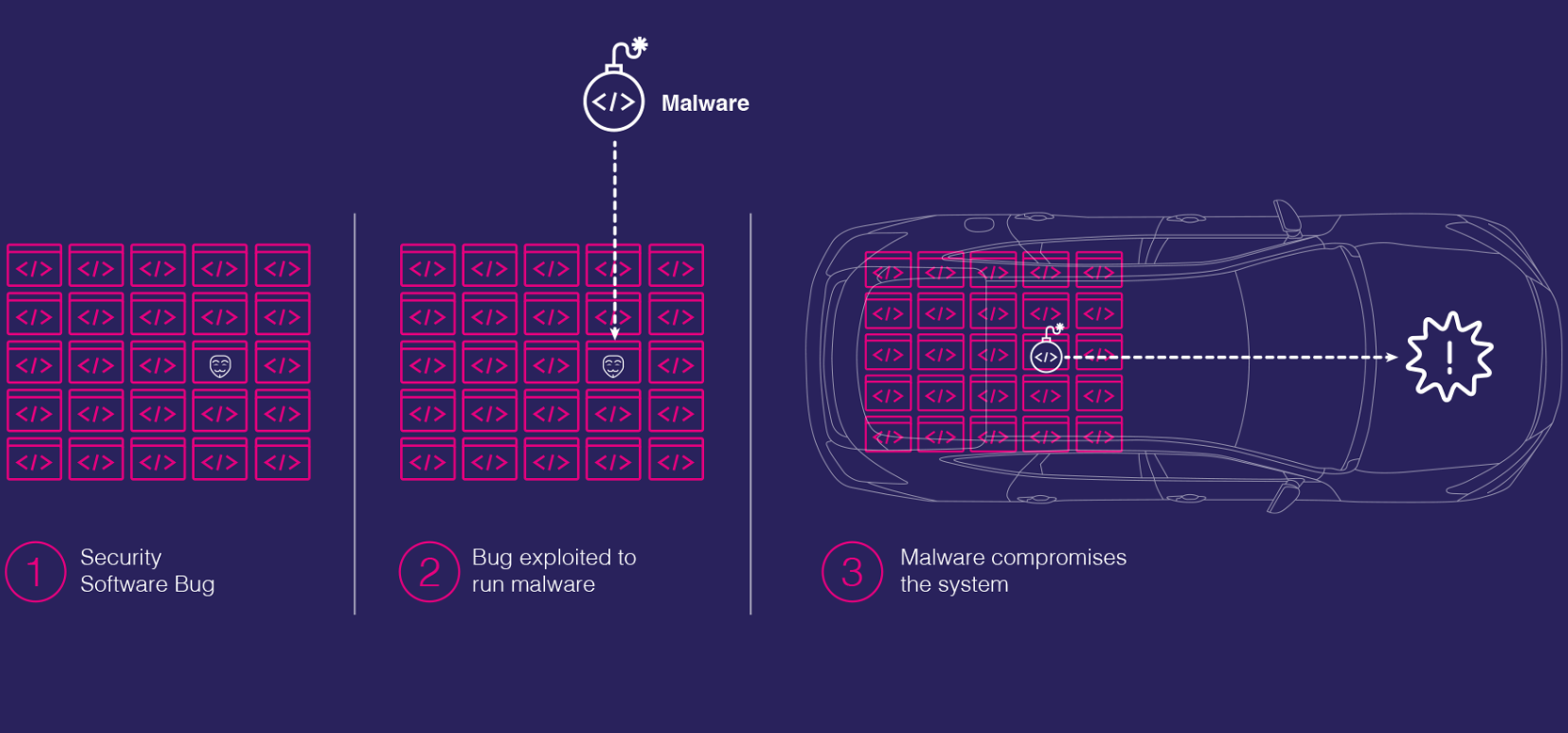
 White hat hackers in March repeatedly demonstrated how security bugs could be exploited in a connected car’s code to infiltrate its safety systems, states Karamba. In the wake of this development, the Federal Bureau of Investigation (FBI), Department of Transportation, and the National Highway Traffic Safety Administration issued a Public Safety Alert (PSA) that highlighted the dangers to new and existing cars on the road. They issued a statement that said, ‘today’s vehicles are increasingly vulnerable to remote exploits that allow a hacker to manipulate critical vehicle control systems’.
White hat hackers in March repeatedly demonstrated how security bugs could be exploited in a connected car’s code to infiltrate its safety systems, states Karamba. In the wake of this development, the Federal Bureau of Investigation (FBI), Department of Transportation, and the National Highway Traffic Safety Administration issued a Public Safety Alert (PSA) that highlighted the dangers to new and existing cars on the road. They issued a statement that said, ‘today’s vehicles are increasingly vulnerable to remote exploits that allow a hacker to manipulate critical vehicle control systems’.
“As vehicle control systems become increasingly automated with everything controlled by software, the probability of code flaws that can be exploited by bad actors for nefarious purposes increases dramatically. Compound this with the growing ubiquity of connected systems including cellular telematics, V2X communications and connected smartphones, and the need to integrate cyber-security protection systems at multiple levels becomes clear,” says says Sam Abuelsamid, senior analyst, Navigant Research.
Abuelsamid opines that the full security solution set will ultimately include electronic architectures designed with security in mind, preventing intrusions to cloud-based transportation services and controlling access to in-vehicle ECUs.
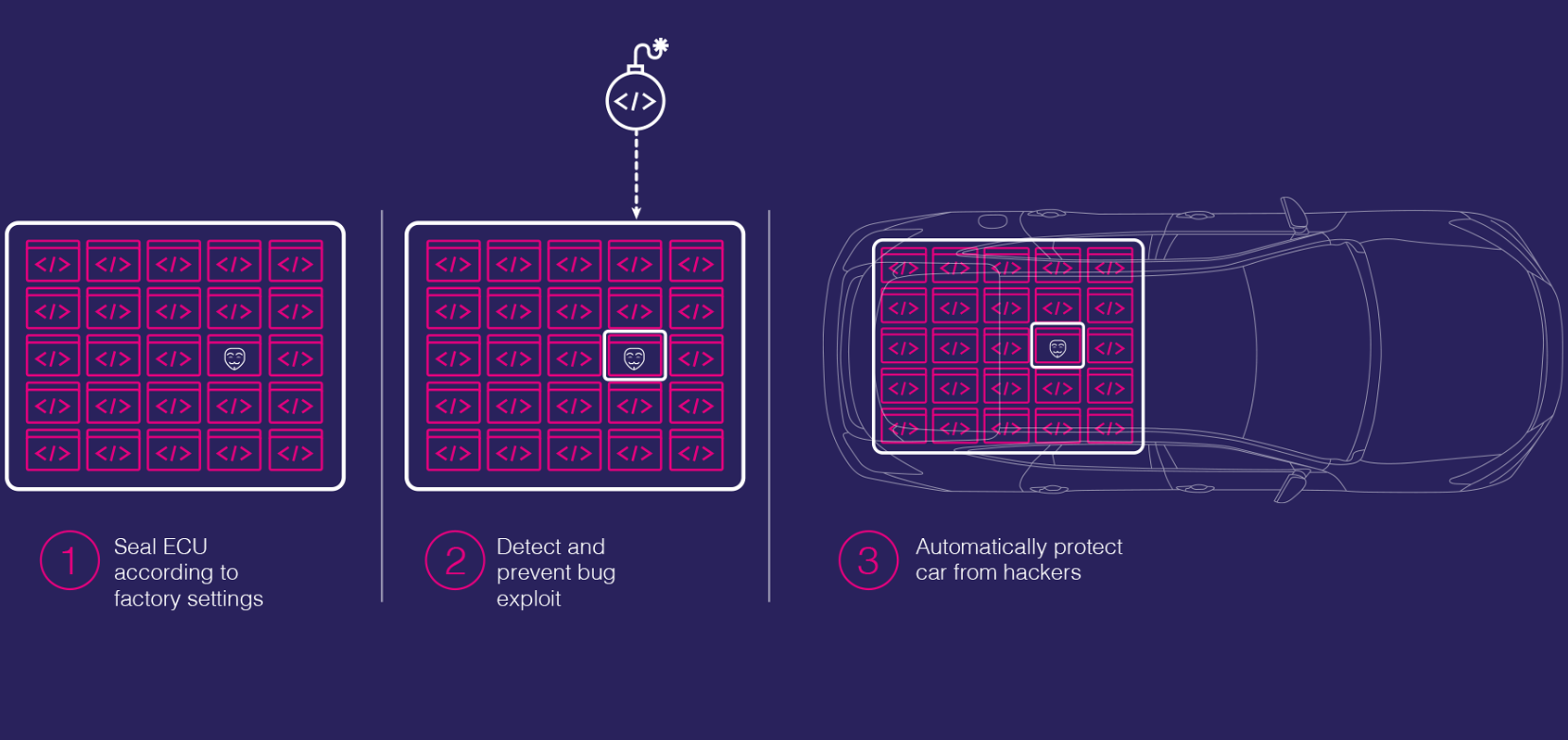
The company claims that since Carwall is part of the ECU software build it is always updated; Carwall protects the code, as is, sealing it to detect and prevent hackers from taking advantage of any security bugs that might be in the controller’s software. Karamba believes that the software’s approach gives car manufacturers and Tier 1 system providers the confidence that ECUs are protected, regardless of any security bugs they may contain, allowing them to keep their product schedules and focus resources on developing new functionality and safety features.
